
Why Cloud Computing Is the Secret Engine Behind Modern Innovation
From AI breakthroughs to startups scaling globally, the cloud is rewriting the rules of what’s possible. Introduction Think about the apps you use every day, Netflix, Zoom, Spotify, or ChatGPT.They all have one thing in common: they run on the cloud. Cloud computing isn’t just an IT trend anymore, it’s the foundation of the digital economy. It allows a small startup to compete with tech giants, lets developers launch products overnight, and helps entire industries reinvent themselves faster than ever before. The New Normal: Building Without Boundaries In the past, launching a new product meant buying servers, installing software, and hiring teams to maintain them. Today, anyone can log into a cloud platform like AWS, Azure, or Google Cloud, spin up servers in minutes, and deploy globally with a few clicks. This shift didn’t just reduce costs, it changed how innovation happens.Developers experiment faster, companies release updates weekly instead of
What is DevOps? A Formal Overview
Development (Dev) and IT operations (Ops) to shorten the software development life cycle. This methodology enables organizations to deliver new features, bug fixes, and updates with high quality and reliability. At its core, DevOps represents a cultural and professional movement that encourages seamless collaboration and communication between these two traditionally siloed teams. The Roles: Development vs. Operations To understand DevOps, it’s essential to define the core roles it unites: Development (Dev): This team consists of software engineers who are responsible for designing, writing, and improving code. Their primary focus is on building new features, fixing bugs, and ensuring the application meets user requirements. Common tools used by development teams include Git, Docker, and IDEs like Visual Studio Code. Operations (Ops): This team is composed of IT professionals and system administrators who manage the infrastructure and ensure software runs reliably. Their responsibilities include deploying applications to servers or cloud platforms, managing

Kali vs. Kali Linux: Clearing the Confusion in Cybersecurity
In the world of cybersecurity, tools and platforms play a crucial role in penetration testing, vulnerability scanning, and ethical hacking. Among these tools, “Kali” and “Kali Linux” are often used interchangeably but do they mean the same thing? Let’s break down the similarities and differences between the two, clear up the confusion, and understand how both fit into the cybersecurity landscape. What is Kali Linux? Kali Linux is a Debian-based Linux distribution specifically designed for cybersecurity professionals. It’s widely used for:Penetration testing, Digital forensics, Security auditing, Ethical hackingDeveloped and maintained by Offensive Security, Kali Linux comes preloaded with over 600 cybersecurity tools like nmap, Wireshark, Metasploit, Burp Suite, and more. It’s considered the go-to OS for ethical hackers and red teamers who need a powerful, open-source platform that’s flexible and battle-tested. So… What is “Kali”?“Kali” is just a shortened or informal name often used to refer to Kali Linux. You’ll
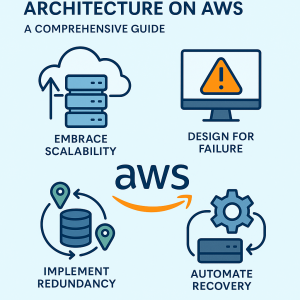
Building a Resilient Architecture on AWS: A Comprehensive Guide
Resilience in cloud computing is the cornerstone of maintaining reliable and uninterrupted digital services. It is the system’s ability to recover from failures and continue operating without significant downtime or data loss. In the dynamic environment of cloud computing, where applications and infrastructure are prone to disruptions, resilience ensures that businesses meet user expectations, maintain trust, and stay competitive. AWS (Amazon Web Services) provides a robust framework and a suite of tools to design and implement resilient architectures. This guide explores key principles, actionable steps, and AWS services that enable the creation of systems designed to withstand failures, recover efficiently, and deliver consistent performance. Resilience involves multiple dimensions that collectively ensure robust system performance. Fault Tolerance refers to systems that can continue functioning despite component failures, ensuring uninterrupted services. High Availability means downtime is minimized, and services remain accessible to users at all times. Disaster Recovery allows systems to recover
